Journalists need to deal, during press work, with a number of programs and applications, such as text editing programs, photo editing programs, video and audio editing programs, compression and decompression programs, and many other programs.
Most of these programs and applications used are paid (not for free),
or free for a short period of time (a trial version running for days or months) or a free copy but with limited privileges/features… until you buy the full version.
To use these programs without buying them, some people resort to software piracy using what is commonly known as a “crack”.
What is “crack”?
It’s a way (which could be called programs) that makes protected programs work perfectly without the need to buy or pay money for those programs. Which means a ”crack” breaks the protection of the program so you can use it completely.
What are the types of “crack”?
There are several types of “crack”, the most important and common:
- Batch
- Keygen (or key/number generator)
We will not go into the details of the way each type works and the difference between these types. We will only provide a simple explanation of its mechanism.
“Batch” or “Keygen” is a program or executable file that is activated after installation of the program to be hacked or for its protection to be broken (cracked), or after the end of the trial period.
* Note, each “crack” is dedicated to one program only \ in some cases the “crack” can be customized for multiple specific programs. Therefore, the crack does not work on all programs.
Who develops the crack?
The crack is made by individuals or companies who discovered how to unlock or break a program’s protection. There are specialized companies/groups working on decrypting the program’s protection and build its own crack.
Is crack free?
There is no rule in this regard, there are some parties that produce free crack and other parties that sell it.
How do we get a crack?
There are several sites on the Internet and several forums specialized in making “cracks” available. The usually have many “cracks” for a large number of programs.
There is also a copy of the programs that have broken protection, called “cracked applications or programs”. There is no need to install the program and install the crack in it, it is enough to install the cracked software to work fully.
Is using “cracked” programs risky?
There is no rule or confirmation that the crack is dangerous or not because it is a program that was produced by mostly unknown parties. Entities can include a malicious file or code inside the crack so the virus will be activated by clicking the crack.
* This is one of the reasons why the crack producer requires disabling the anti-virus before activating or installing the crack. We do not recommend to disable a device’s antivirus in any case, especially when dealing with a program written by an unknown party or unverified source.
What is the risk posed by the virus resulted from crack??
There is a large number of threats posed by the virus. Among them:
- Corruption/destruction of the operating system;
- Full control of the device remotely (so that the party who developed the virus, for example, turn on the camera, listen to the microphone, take screenshots for the desktop, or transfer files to and from the device … , meaning, the hacker can access the entire device as if they sit in front of it, without the owner’s knowledge);
- Use your device to perform technical attacks on specific sites or some entities.
* Note, the virus effect is not necessarily immediate, the virus can stay inside the device for long periods before it starts functioning.
Is there an anti-virus capable of protecting devices from a cracked program’s dangers?
Downloading anti-virus on the device is very necessary (for all types of devices and operating systems)
* We can not emphasize enough the need to update the anti-virus every period of time (every week or every month maximum)
But even the anti-virus isn’t able to detect all types of threats, including threats or viruses integrated with the crack. However, and if the user insists on using a “cracked” program it might be useful to run a scan of the file using the anti-virus.
E.g: The following image shows an anti-virus program that prevents three applications included in a crack designed to break the copy of Office 2013 from accessing the camera. That means that the entity who created the crack has integrated a program that can access the camera, enabling them to take pictures and videos and send them to the owner of the crack without the knowledge the owner of the device.
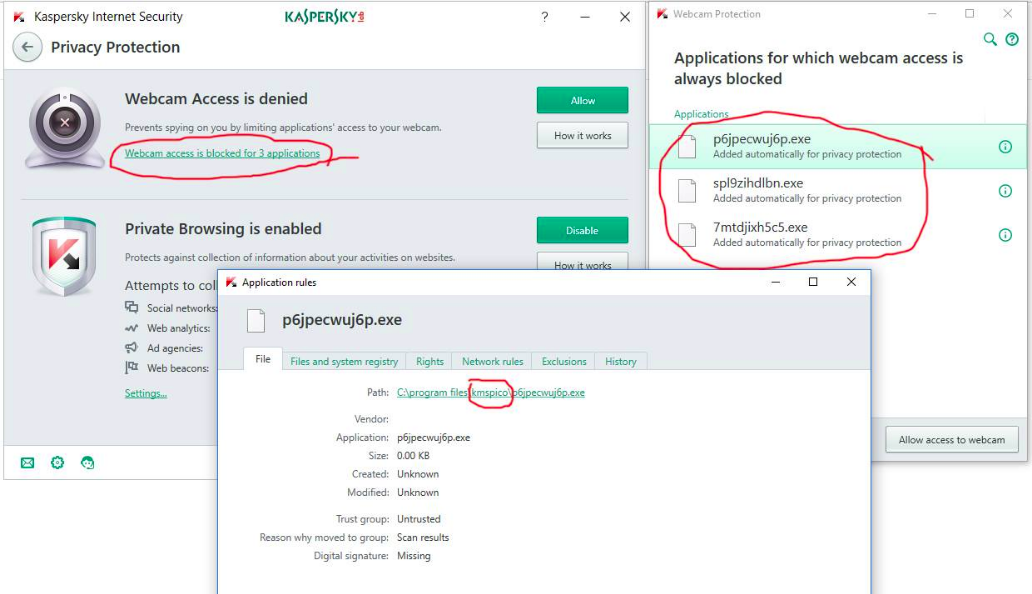
Is creating or using a crack legal?
Developing or using a crack or “cracked programs” is illegal in most countries and falls under piracy. The penalty for developing or using the crack varies from country to another. The penalty might be financial or it may even be imprisonment.
What is the alternative of using cracked programs?
Most of the paid programs – which need to be purchased or break its protection by using (crack) – have free alternative programs.
* What are the free applications or programs that use free software?
A brief article about free software on Adif Foundation website
For example:
- Microsoft Office programs … There is a free alternative: LibreOffice or another alternative: OpenOffice
- WinRAR … has a free and secure alternative: 7ZIP
- Audio editing software … There is a free and secure alternative: Audacity
- Photoshop for photo processing … It has a free and secure alternative: GIMP
Windows operating system (which is not free) has several free alternatives such as the Ubuntu operating system,
* ALTERNATIVETO can also be used to find free alternative programs for a large number of common programs: https://alternativeto.net/
The following site can also be used too: https://bartvandewoestyne.github.io/osswin to find a huge number of free programs classified by type (audio processing programs – image processing programs – video processing programs – compression and decompression files programs – design programs … and other types of programs).
Some free programs cannot be as easy to use as paid programs, or people are used to a certain programs and do not want to replace it with another program because they are used to work on specific ones.
So they prefer software piracy instead of using the alternative program … In the end, it all comes down to g is about how people evaluate themselves … Which is the priority for them:
– Safety (use free software)?
or
– Easiness (using crack) thus exposing themselves to risks?! …
* Let us remember any program that we are familiar with now and work easily on it, we did not know how to handle it well on first useat first… But through practice, it became easier to handle the program (Windows or Word or Photoshop for example).
So any new program can be confusing at first, but certainly will be easy to use after practicing for a while.
Most free programs have tutorials on the Internet
*Note:
This article was written and edited using free software
– The article was written and edited using LibreOffice Writer (free), an alternative to the non-free Microsoft Word
– The images were edited by using GIMP (free), an alternative to the non-free Photoshop
Via Linux (free), an alternative to the non-free Windows.
* All organizations and press groups are advised to include in their policies a policy for dealing with programs and applications and not to use “crack” or pirated software to maintain their security and the security of their files and data.






