How to protect our devices and data from hacking or surveillance
Due to security and technical threats and dangers that journalists face, the question is how to protect our devices and/or data from hacking or surveillance?
And the reason is that there is no application or software (or set of applications or programs) than can fully protect the device!
The protection of digital privacy and devices is: first and foremost, through “technical awareness raising” about the threats we could encounter. Later comes security programs and applications that help protect our devices, data and digital privacy.
What is technical awareness raising?
Raising technical awareness comes through knowing the threats and risks that we are exposed to or may be exposed to, and the targeting mechanisms that we can be exposed to … which we will mention through the following points:
– The first point
As technical experts, we talk about the need to download mobile or tablet applications from the official stores of the devices (Android and IOS). Applications downloaded from another location/site may have malware. But, at the same time, are all the apps on Google and Apple stores safe?
The answer is “no”! Because although Google and Apple are scanning apps that are uploaded to their store, neither company does a security audit to all applications! Because very large resources are required due to the very large number of “daily growing” applications, in addition to the continuous updates of a very large number of these applications.
Therefore, every now and then the store deletes certain applications that are found to be unsafe, but we cannot be sure that all the remaining apps on the store are safe.
The first conclusion
Google and Apple must be relied on to install applications. At the same time, not all apps found inside the store should be trusted.
________________________________________
– The second point
Because of ongoing technical threats and challenges, people ask their friends about programs or applications that could help them protect their devices.
In our work as technical experts, we constantly notice that people use (install) a large number of security programs on their devices that are passed on and advised among their friends. A large number of these programs and applications are unsafe. Especially those applications that have extensive access permissions within the devices! Some apps requires access to things like access to the geographical location – access to the camera and microphone device – access to the internal phone memory and external memory card – access to contacts on the phone – access to the calls log … and other access permissions that affect and violate the privacy of the owner of the device. Other than that, some applications contains malware that take full control of the device remotely, including transferring files to and from the device (phone, computer, or tablets)
The second conclusion
Our personal trust in people should not make us trust their technical choices. Unless they are technical experts.
Some friends suggest us in good faith the programs and applications they have used, but these programs are not necessarily safe. For this reason, in case of need for a technical question or request, the question should be directed to people or organizations with technical expertise that you trust.
________________________________________
– The third point
As in the previous point, due to the need for technical protection, search engines (such as Google) are used to search for software and applications that help protect devices.
It is no secret that the Internet contains a large number of sites and forums that talk about technical matters and information security, especially groups on “Facebook”.
A number of these sites, forums and groups are good sites and contain useful and reliable technical advices, but the largest number of them contain false information, especially sites where the blog or blogger or the people who write the material does not have good technical background or technical information.
It has been noted that a large number of sites, forums, groups and people promote some programs and applications as safe programs or as programs that protect devices, while in fact a number of these programs and applications are useless programs or programs that contain malicious software.
On the other hand, some parties exploit the need for people to protect their privacy and digital security, they promote certain applications and programs as protection or security programs, while in fact they are programs that violate privacy and eavesdrop on devices and steal data and information. For example, the “Secure Mail” application that leaks Gmail account login data to a server used by attackers. The “%200iLoud” application is promoted as an application that doubles the sound of the phone but instead it finds the location the phone even if the GPS feature is disabled.
The “IndexY” application promoted as an application for showing the caller’s name (similar to “Truecaller”) but it actually copies the details of calls made on the phone and sends them to a server used by the attackers. In addition to many other applications that are promoted or appear when an event occurs, such as in Syria a while ago when communications started to stop and interrupted via WhatsApp, a number of organizations and individuals have promoted alternative but unsafe communication applications and unsecure override blocking applications (VPN).
A number of activists had previously received messages through several communication programs containing some links that claim to contain encryption programs, anti-virus protection programs and other protection programs as shown in the following picture.
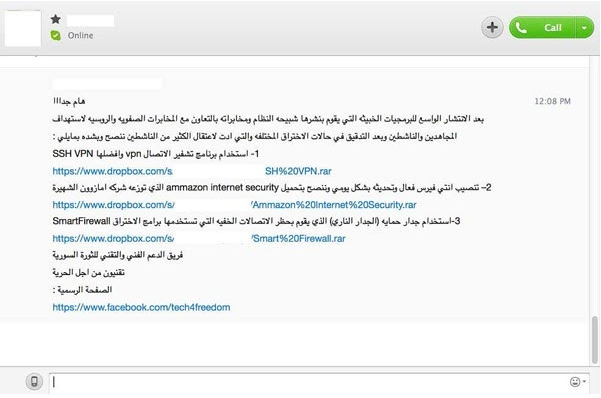
In fact, these links turned out to contain malware!
Another example.
On one of the technical groups, someone asked a question: “If I want to change the number I use on Whatsapp, will my conversations be deleted?”
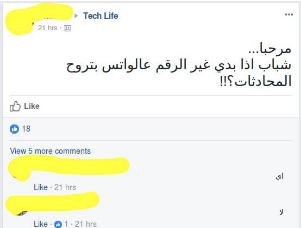
Note, as in the picture, that the person got two contradictory answers! The first answer is that conversations are not retained when the number is changed. The second answer is that conversations remain on the device when the number is changed.
The example was used to say that in groups, forums, or even sites with technical content, they may contain incorrect answers/tips, some of which may be harmful!
The third conclusion
Search engines show us a large number of sites and forums talking about or containing the topic we are looking for, but the use of large search engines such as “Google” or other search engines, does not mean that the sites or search results that appear to us are credible sites or that they are promoting for a secure software. Also, no news or advice, especially from unreliable or unknown parties, should be trusted. Instead, you should always ask for help from people or organizations with technical expertise that you trust.
- Not installing a security program on the device is much better than installing an unsafe one. Because the lack of security software can put your device at risk of being compromised, but the presence of unsafe applications will certainly put your device at risk.
________________________________________
– The fourth point
Due to the need to use a large number of programs and applications that are not necessarily free, and sometimes expensive (such as the Windows operating system, Microsoft Office programs, Photoshop design program, WinRAR compression and decompression and many other applications and programs), people resort and resort to use crack programs that make protected or non-free programs work without having to pay for them.
But most “crack” programs are unsafe and dangerous tools on the devices because of the malicious software it contains.
The fourth conclusion
If you cannot purchase licenses for the required software, you should not use pirated software. Alternatively, you can use free software, applications and free operating systems that use open source software.
The following link contains details of the risks of “crack” or pirated software, and links to some safe alternative programs
________________________________________
– The fifth point
One of the most common methods used to hack devices is to use messages that contain malicious links and files (attachments). The victim is tricked into clicking a link inside the message, which opens a site or redirects to a malicious site that leads to the installation of malicious software on the device. Or the victim is tricked into downloading the attached file, which in turn loads malware onto the device. Which leads to hacking or monitoring and control the device remotely.
These messages can be via email or via SMS or via communication programs such as Whatsapp, Signal, Wire, Telegram, Facebook Messenger, Skype…. And other communication applications. Or through ads with a QR code.
Conclusion
Any message with links and attachments, especially messages from unknown or untrusted parties, should be questioned and not responded to.
Upon receiving a suspicious message from a contact we know, the identity of the sender must be ascertained, since in a large number of detected hacks, messages containing malicious links were sent from hacked accounts, accounts impersonating somebody known to the victim, or impersonating a general person.
The following link contains details about phishing messages and how to deal with them
________________________________________
Finally, there is no radical solution or tool / program / application that fully protects the device, and no devices are protected from hacking or technical threats.
Basic protection is through the use of devices as mentioned in the preceding paragraphs. It is also necessary to use some protection programs and applications such as anti-virus software.
The following link contains an explanation of how viruses work and how to avoid their dangers
You should also avoid installing unsafe web browser extensions, and use some plugins that help keep your browser private and secure.
The following link contains an explanation of what are the web browser plugins and suggest some necessary plugins
It is also important to use connection encryption applications.
The following link contains a number of encryption programs and how they work
A set of notes …
* The presence of protection programs on the device, may slow down the work of the device, but they are necessary and important
* In case of malware or malicious software on the device, the protection software and safe use of the device will not be effective! Therefore, if you experience any unusual behavior in the device or are concerned about any clicked link or file downloaded to the device, it is best to reset the device (Format) and reconfigure it. * This must be done when purchasing / possessing a used device or used from another person before.
* Some stores may install malware on the new devices while setting it up. Therefore, and in order to avoid the matter, when purchasing / possessing a new device, it must be confirmed that the first startup was run by us and it was not previously turned on (we can know that … When the device is turned on for the first time, a welcome message appears and the device asks us to start the setup and choose the language and the main account for the device) If the setup options for the device do not appear and enter directly to the desktop or software interface, then the device must be reset and reformatted again.
End





