Phone application’s permissions
When you install apps on your phone, they ask for “permissions” on the phone. Such as: access to contacts – access to device memory – access to geographic location – access to the camera of the phone – access to the call log … And many other permissions.
Google and through the application “Google Store” obliges the owners of the applications to disclose the permissions required by the application, thus the permissions required by the application appear when installing the application and can be reviewed before installation.
For applications on IOS phones, permissions are required after the application is installed
What is the purpose of the permissions requested by apps?
Permissions allow the application to access the options and information that allow it to do its job. Example: When installing an application for written and voice communication (such as Whatsapp, Signal, Wire or Telegram), these applications need access to the keyboard (so that we can write messages within the application). Need access to the microphone (so we can make a voice call or send voice messages from within the app). Need access to the camera (so we can make a video call or shoot from within the app). Need access to contacts (so we can identify contacts and communicate with them through the application).
Or when you install an app to edit images, the app needs access to the photo studio and device memory (so we can select and save the image) and some need access to the keyboard (to add text to the images).
Do apps require only the permissions they need?
No! A number of applications will ask for permissions that are not needed for the application.
Example: An app that controls the device’s flash light
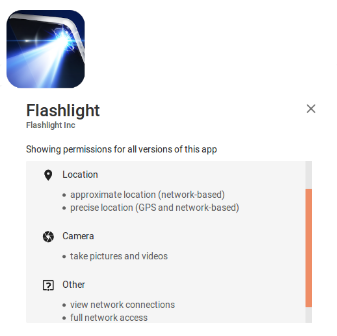
It is noted that the application requests access to the geographical location, access to the camera and to take pictures, and full access to the telephone network.
They are unjustified permissions for the application only needs access to the device’s flash light.
Some applications request unjustified permissions. Its purpose is to gather information for several reasons, including propaganda purposes. And some applications will have a sly purpose.
In Android versions prior to 6.0, it was not available to control permissions for all apps, and we had to use an app that helps us revoke the permissions of the apps. As of version 6.0 users can control the permissions requested by the applications (cancel and activate permissions for each application). As with IOS devices (iPhone).
The article on the link here contains details about controlling app permissions
Although Google forces the owners of the applications to reveal the permissions required by the application, some applications were able to bypass the Android operating system protocol and get the user’s data without asking for permissions details in the link here
For this and other reasons, when you download an app on your phone you should:
This paragraph is taken from material on your safety wiki site with some modification
- Download apps from trusted app stores like the Google Play Store. Do not download apps from suspicious stores or sites without knowing their source.
- Make sure from the identity and credibility of the developer of the application … Also you should not install unknown applications.
- Read the reviews well to learn more about the application, try to search for reviews that address the topics of privacy and security. Do not download and install applications with negative reviews regarding privacy and security.
- Review the permissions requested by the app well. Do not install any application that requires more permissions than it needs to accomplish its work, or that requests permissions that may be a risk to your privacy and security.
A detailed table of the most important permissions for the Android operating system
This paragraph is taken from material on Salamatech wiki
| Dangers | Explanation | Permission |
| This is a dangerous permission and should be granted only to communication applications such as Skype for example | Making phone calls by itself | Directly call phone numbers |
| This is a dangerous permission and should only be granted to known messaging applications | Sending SMS messages | Send SMS messages |
| This permission means that the app can transfer, modify, or delete data from the storage. And it’s an important permission many applications that store data on your device will need | Modify or delete USB storage | |
| Should be granted only to social media and messaging apps | Reach and modify contacts. Needed by social media and communication apps | Read and change my contacts |
| Should not be granted to apps that has nothing to do with browsing the internet, such as games for example | This permission is needed by web browsers and some social media apps | Bookmark web pages and read web history |
| Should not be granted to applications unless you are sure of what you are doing | Read other application’s log data. It’s an important permission and not needed in general | Read sensitive log data |
| You should be careful when granting this permission because it could means exposing your geographic location to the party that is responsible for the app | Knowing the status of the phone, and it is a double-edged permission. Applications need it for the phone to be able to stop the application and receive a call, but also through it the application gets the IMEI and IMSI numbers and thus become able to determine the approximate geographical location. And maybe send it to the app. | Read phone state and identity |
| You should be careful when granting this permission because it could means exposing your geographic location to the party that is responsible for the app | Determine your geographical location through the global navigation system that works by satellite and needed by navigation applications, maps and prayer times, for example. | Find GPS Location |
| You should be careful when granting this permission because it could means exposing your geographic location to the party that is responsible for the app | Determine your geographic location through networks connected with your smartphone. Needed by navigation applications, maps and prayer times, for example. | Coarse Network-based Location |
| Can turn on the Bluetooth connectivity in your device. Needed applications that transmit data wirelessly via Bluetooth device. | Create Bluetooth connections | |
| This permission carries a lot of risks as it enables applications to connect to the Internet without your knowledge. Be careful in granting this permission because there are applications that don’t need internet to do its purpose. | This permission allows the application to use the Internet. It is needed by many applications related to Internet services. | Full Internet access |
| View Network status / Wi-Fi state | ||
| If, for example, a game asks for this permission, then you will have to not use this app or game because it’s suspicious | It’s a sensitive permission needed by all apps like Facebook, Google, and Twitter | Manage Accounts |
| Use credentials | ||
| Malicious apps may use this permission to download and install more malicious files on your device, so be careful not to give it to apps that aren’t related to the Google Store. | This permission allows the app to download other apps. Like in the Google Play app, for example | Install Packages (Apps) |
| With this permission, the app can prevent your phone from sleeping. Video and audio players normally need this permission. | Prevent phone from sleeping | |
| This permission lets the app know if account sync is enabled and works in the background away from the UI. | Read sync settings | |
| Some malicious apps may use it to spy on you. The applications with no reason or need for that permission must be dispensed. Here you can also check the Cam Cover | This permission allows the app to turn on the camera and take photos and videos | Take photos or video |
End





